| Version 17 (modified by , 3 years ago) ( diff ) |
|---|
Kali
Offical Kali Linux images are now provided by Offensive Security for both Ventana and Newport.
Build-scripts can be found here:
- Ventana
- Newport
- Create your own - kali-linux-arm-chroot
The Ventana prebuilt image can be downloaded from here, ARM images > Gateworks.
Note: Offical images use Gateworks kernel repos.
What is Kali
Kali Linux (formerly known as BackTrack Linux) is an open-source, Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing. Kali Linux contains several hundred tools targeted towards various information security tasks, such as Penetration Testing, Security Research, Computer Forensics and Reverse Engineering. Kali Linux is a multi platform solution, accessible and freely available to information security professionals.
Kali Linux was initially released on the 13th March 2013 as a complete, top-to-bottom rebuild of BackTrack Linux, adhering completely to Debian development standards.
Reference: https://www.kali.org/docs/introduction/what-is-kali-linux/
Kali on Gateworks
Official instructions:
The following instructions can be used on Ventana or Newport family boards.
Requirements:
- 16GB SD card or larger (Class 10 recommended)
- Gateworks SBC Ventana or Newport
- Linux Desktop Workstation
- Wireless radio capable of packet injection (Alfa AWPCIE-AX200U recommended)
- Antennas
Installing Kali to an SD card
Insert SD card into Linux workstation, use "dmesg" to check the device name udev has assigned, for example "/dev/sdb".
Some operating systems will auto-mount block storage devices, the partitions must be unmounted in order to write directly to the volume:
umount /dev/sdb?
Write image to SD card:
xzcat kali-linux-1-newport.img.xz |sudo dd of=/dev/sdb bs=4M status=progress
The card is now imaged with Kali. Because the partitions have already been unmounted simply remove the card.
Booting the SD card
To boot from the SD card on the Gateworks "boot_targets", or "bootdevs" need to be set so the SD card has priority over the flash.
Break out in the bootloader:
For Newport:
GW6204-B> setenv boot_targets mmc1 mmc0 usb0 scsi0 GW6204-B> saveenv
For Ventana:
Ventana > setenv bootdevs mmc Ventana > print bootdevs bootdevs=mmc Ventana > saveenv Saving Environment to NAND... Erasing NAND... Erasing at 0x1000000 -- 100% complete. Writing to NAND... OK Ventana >
Reboot the SBC.
Once Kali is loaded login, username "kali", password "kali".
Verify that your network interfaces are available:
ls /sys/class/net
Check your radio is capable of working on the channels that will be monitored:
iw phy phy0 channels
Install Metasploit Framework
Metasploit framework is an open source tool which can be used to probe systematic vulnerabilities on networks and servers.
Metasplot features:
- Command shell payloads that enable users to run scripts or random commands on a host
- Dynamic payloads that allow testers to generate unique payloads
- Meterpreter payloads that allow users to VMC and monitor sessions and upload and download files
- Static payloads that enables port forwarding and communications between networks
Offensive-Security offers a free online course for learning Metasploit: https://www.offensive-security.com/metasploit-unleashed/
To install Metasploit on Gateworks:
- Update your system
apt-get update
- Install curl
sudo apt-get install curl -y
- Download and install Metasploit
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && \ chmod 755 msfinstall && \ ./msfinstall
Aircrack-ng
Aircrack-ng is a suite of tools that can be used to access a WiFi networks security.
It focuses on different areas of WiFi security:
- Monitoring: Packet capture and export of data to text files
- Attacking: Replay attacks, deauthentication, fake access points and others via packet injection
- Testing: Checking WiFi cards and driver capabilities (capture and injection)
- Cracking: WEP and WPA PSK (WPA 1 and 2)
Reference: https://www.aircrack-ng.org/
For deauthentication the wifi adapter will need to be capable of packet injection.
To test if packet injection is available:
sudo aireplay-ng --test wlan0mon
Capturing packets
In order to capture packets airmon-ng is used to create a monitor interface.
To begin connect to the board using SSH (this is important later).
Kill processes that may interfere with airmon-ng:
sudo airmon-ng check kill
Start the monitor interface:
sudo airmon-ng start wlan0 #this command creates the "mon" interface "wlan0mon".
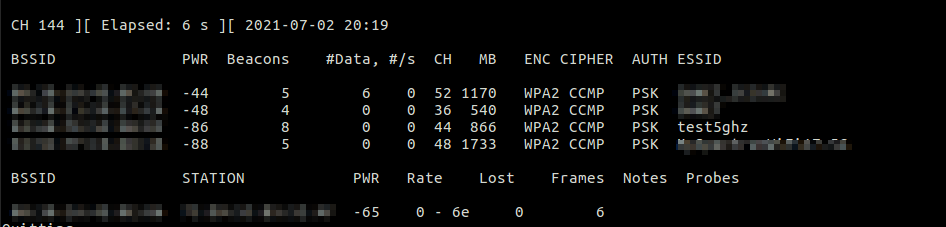
Kick off airodump-ng to start capturing packets. Note, airodump-ng by default will only monitor on 2.4Ghz, use the "--band a" switch to enable 5ghz monitoring.
sudo airodump-ng --band a wlan0mon
Getting help with Kali
Please direct all Kali Linux related questions to the forums:
Feel welcome to contact support@gateworks.com for questions specific to Gateworks.
Attachments (9)
-
Kali.png
(27.1 KB
) - added by 3 years ago.
kali logo
-
thegibson.png
(470.1 KB
) - added by 3 years ago.
the gibson
-
handshake.png
(23.9 KB
) - added by 3 years ago.
handshake
-
test5ghz.png
(31.1 KB
) - added by 3 years ago.
scan
-
single out SSID.png
(20.0 KB
) - added by 3 years ago.
single out ssid
-
aircrack.png
(20.5 KB
) - added by 3 years ago.
aircrack
-
msf.png
(101.9 KB
) - added by 3 years ago.
msf
- laptopsecurity.jpg (65.6 KB ) - added by 3 years ago.
- kali.jpg (178.6 KB ) - added by 3 years ago.
Download all attachments as: .zip